Posts Tagged ‘Education’
Presentations: Starting your security career – where can you go?
I gave a talk on career planning in Information Security at Abertay University on the 16th of January 2013.
Securi-Tay is an annual security conference organised by students at Abertay and is a very well organised and run event – could put some professional conferences to shame!
The talk went down very well, with a lot of discussion spinning off afterwards, and the odd additional visitor to Sec.SE
Most of the video should be straightforward, but a couple of the slides may be hard to read so I have included them here:
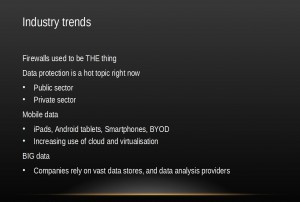
Slide 8, industry trends:
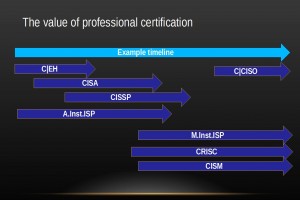
Slide 13, some useful certifications:
Securi-Tay 2 Conference
Spent January 16th up in Dundee, at the University of Abertay, at Securi-Tay 2. It was a very well run conference – it was organised by students on the Ethical Hacking and Countermeasures course, but was better organised than some professional conferences I have been to.
I saw some excellent speakers, and gave a talk on career planning in information security, so mine was by far the least technical talk there.
Highlights for me:
- Rory McCune gave an excellent talk on automation of security testing, both as a standard practice to make life easier, but to help consistency and standards in testing.
- Marion McCune presented on using the Windows Surface for security testing, which I think surprised everyone with the power of an ARM powered tablet.
- Graham Sutherland’s talk on attacking office hardware ranged from simple and relatively harmless, to pretty hardcore hacking via chip removal and analysis. Excellent fun, but sadly there was no party hat…
- Nick Walker’s talk on Android Security Assessments, while slightly too technical for me, was very interesting, and reminded me to pop Cyanogenmod on my Galaxy S3 this weekend.
- The” Rory track” – of the two lecture theatres, one had 3 Rorys presenting, which just goes to confirm one of the Memes of Meta…
And the good folks at Securi-Tay kindly donated this bright red t-shirt to my con swag collection, so I went home even happier!
QoTW #41: Why do we lock our computers?
Iszi chose this week’s question of the week, Tom Marthenal‘s “Why do we lock our computers?” – as Tom puts it:
It’s common knowledge that if somebody has physical access to your machine they can do whatever they want with it, so what is the point?
This one attracted a lot of views, as it is a simple question of interest to everyone.
Both Bruce Ediger and Polynomial answered with the core reason – it removes the risk from the casual attacker while costing the user next to nothing! This is an essential factor in cost/usability tradeoffs for security. From Bruce:
The value of locking is somewhat larger than the price of locking it. Sort of like how in good neighborhoods, you don’t need to lock your front door. In most neighborhoods, you do lock your front door, but anyone with a hammer, a large rock or a brick could get in through the windows.
and from Polynomial:
An attacker with a short window of opportunity (e.g. whilst you’re out getting coffee) must be prevented at minimum cost to you as a user, in such a way that makes it non-trivial to bypass under tight time constraints.
Kaz pointed out another essential point, traceability:
If you don’t lock, it is easy for someone to poke around inside your session in such a way that you will not notice it when you return to your machine.
And zzzzBov added this in a comment:
…few bystanders would question someone walking up to a house and entering through the front door. The assumption is that the person entering it has a reason to. If a bystander watches someone break into a window, they’re much more likely to call the authorities. This is analogous with sitting down at a computer that’s unlocked, vs physically hacking into the system after crawling under a desk.
It removes a large percentage of possible attacks – those from your co-workers wanting to mess with your stuff – thanks enedene.
So – protect yourself from co-workers, casual snooping and pilfering and other mischief by simply locking your machine every time you leave your desk!
Liked this question of the week? Interested in reading it or adding an answer? See the question in full. Have questions of a security nature of your own? Security expert and want to help others? Come and join us at security.stackexchange.com.
QotW #12: How to counter the statement: “You don’t need (strong) security if you’re not doing anything illegal”?
Ian C posted this interesting question, which does come up regularly in conversation with people who don’t deal with security on a daily basis, and seems to be highlighted in the media for (probably) political reasons. The argument is “surely as long as you aren’t breaking the law, you shouldn’t need to prevent us having access – just to check, you understand”
This can be a very emotive subject, and it is one that has been used and abused by various incumbent authorities to impose intrusions on the liberty of citizens, but how can we argue the case against it in a way the average citizen can understand?
Here are some viewpoints already noted – what is your take on this topic?
M’vy made this point from the perspective of a business owner:
Security is not about doing something illegal, it’s about someone else doing something illegal (that will impact you).
If you don’t encrypt your phone calls, someone could know about what all your salesman are doing and can try to steal your clients. If you don’t shred your documents, someone could use all this information to mount a social engineering attack against your firm, to steal R&D data, prototype, designs…
Graham Lee supported this with a simple example:Commercial confidential data…could provide competitors with an advantage in the marketplace if the confidentiality is compromised. If that’s still too abstract, then consider the personal impact of being fired for being the person who leaked the trade secrets.
So we can easily see a need for security in a commercial scenario, but why should a non-technical individual worry? From a more personal perspective, Robert David Graham pointed this outAs the Miranda Rights say: “anything you say can and will be used against you in a court of law”. Right after the police finish giving you the Miranda rights, they then say “but if you are innocent, why don’t you talk to us?”. This leads to many people getting convicted of crimes because it is indeed used against them in a court of law. This is a great video on YouTube that explains in detail why you should never talk to cops, especially if you are innocent: http://www.youtube.com/watch?v=6wXkI4t7nuc
Tate Hansen‘s thought is to ask,
“Do you have anything valuable that you don’t want someone else to have?”
If the answer is Yes then follow up with “Are you doing anything to protect it?”
From there you can suggest ways to protect what is valuable (do threat modeling, attack modeling, etc.).
But the most popular answer by far was from Justice:
You buy a lock and lock your front door if you live in a city, in close proximity to hundreds of thousands of others. There is a reason for that. And it’s the same reason why you lock your Internet front door.
Iszi asked a very closely linked question “Why does one need a high level of privacy/anonymity for legal activities”, which also inspired a range of answers:
From Andrew Russell, these 4 thoughts go a long way to explaining the need for security and privacy:
If we don’t encrypt communication and lock systems then it would be like:
Sending letters with transparent envelopes. Living with transparent clothes, buildings and cars. Having a webcam for your bed and in your bathroom. Leaving unlocked cars, homes and bikes.
And finally, from the EFF’s privacy page:
Privacy rights are enshrined in our Constitution for a reason — a thriving democracy requires respect for individuals’ autonomy as well as anonymous speech and association. These rights must be balanced against legitimate concerns like law enforcement, but checks must be put in place to prevent abuse of government powers.
A lot of food for thought…
QotW #7: How to write an email regarding IT Security that will be read, and not ignored by the end user?
A key aspect of IT and Information Security is the acceptance piece. People aren’t naturally good at this kind of security and generally see it as an annoyance and something they would rather not have to deal with.
Because of this, it is typical in organisations to send out regular security update emails – to help remind users of risks, threats, activities etc.
However it is often the case that these are deleted without even being read. This week’s question: How to write an email regarding IT Security that will be read, and not ignored by the end user? was asked by @makerofthings and generated quite a number of interesting responses, including:
- Provide a one line summary first, followed by a longer explanation for those who need it
- Provide a series of options to answer – those who fail to answer at all can be chased
- Tie in reading and responding to disciplinary procedures – a little bit confrontational here, but can work for items such as mandatory annual updates (I know various organisations do this for Money Laundering awareness etc)
- Using colours – either for the severity of the notice, or to indicate required action by the user
- Vary the communications method – email, corporate website, meeting invite etc
- Don’t send daily update messages – only send important, actionable notices
- Choose whose mailbox should send these messages – if it is critical everyone reads it, perhaps it should come from the FD or CEO, or the individual’s line manager
- Be personal, where relevant – users who receive a few hundred emails a day will happily filter or delete boring ones, or those too full of corporate-speak. Impress upon users how it is relevant to them
- Add “Action Required” in the subject
It is generally agreed that if it isn’t interesting it will be deleted. If there are too many ‘security’ emails, they’ll get deleted. In general, unless you can grab the audience’s attention, the message will fail.
Having said that, another take on it is – do you need to send all these security emails to your users? For example, should they be getting antivirus updates or patch downtime info in an email every week?
Can users do anything about antivirus, or should that be entirely the responsibility of IT or Ops? And wouldn’t a fixed patch downtime each week that is listed on the internal website make less of an impact on users?
Thinking around the common weak points in security – such as users – for most actions can make much more impact when you actually do need the users to carry out an action.
Associated questions and answers you should probably read:
What are good ways to educate about IT Security in a company?
Some More BSidesLV and DEFCON
Internet connectivity issues kept me from being timely in updating, and a need for sleep upon my return led me to soak up all of the rest of BSides and DEFCON. That means just a few talks are going to be brought up.
First, there’s Moxie Marlinspike‘s talk about SSL. In my last post, I had mentioned that I thought SSL has reached the point where it is due to be replaced. In the time between writing that and seeing his talk, I talked with a few other security folk. We all agreed that DNSSEC made for a better distribution model than the current SSL system, and wondered before seeing Moxie’s presentation why he would add so much more complexity beyond that. The guy next to me (I’ll skip name drops, but he’s got a security.stackexchange.com shirt now and was all over the news in the last year) and I talked before his presentation, and at the end agreed that Moxie’s point about trusting the DNS registry and operators to not change keys could be a mistake.
Thus, we’re still in the world of certificates and complicated x.509 parsing that has a lot of loopholes, and we’ve moved added something that the user needs to be aware of. However, we have one solid bonus: many independent and distributed sources must now collaborate to verify a secure connection. If one of them squawks, you at least have an opportunity to be aware. An equally large entry exists in the negative column: it is likely that many security professionals themselves won’t enjoy the added complexity. There’s still a lot of research work to be done, however the discussion is needed now.
PCI came up in discussion a little bit last year, and a lot more this year. In relation, the upcoming Penetration Testing Execution Standard was discussed. Charlie Vedaa gave a talk at BSides titled “Fuck the Penetration Testing Execution Standard”. It was a frank and open talk with a quick vote at the end: the room as a whole felt that despite the downsides we see structures like PCI and the PTES, we were better off with them than without.
The line for DEFCON badges took most people hours and the conference was out of the hard badges in the first day. Organizers say it wasn’t an issue of under-ordering, but rather that they had exhausted the entire commercial supply of “commercially pure” titanium to make the badges. Then the madness started…
AT&T’s network had its back broken under the strain of DEFCON resulting in tethering being useless and text messages showing up in batches sometimes more than 30 minutes late. The Rio lost its ability to check people into their hotel rooms or process credit cards. Some power issues affected the neighboring hotel at a minimum — Gold Coast had a respectable chunk of casino floor and restaurant space in the dark last evening. The audio system for the Rio’s conference area was apparently taken control of and the technicians locked out of their own system. Rumors of MITM cellular attacks at the conference, and now days later in the press abound. Given talks last year including a demonstration and talks this week at the Chaos Computer Camp, the rumors are credible. We’ll wait to see evidence, though.
DEFCON this year likely had more than 15,000 attendees, and they hit the hotel with an unexpected force. Restaurants were running out of food. Talks were sometimes packed beyond capacity. The Penn and Teller theater was completely filled for at least three talks I had interest in, locking me outside for one of them. The DEFCON WiFi network (the “most hostile in the world”) suffered some odd connectivity issues and a slow-or-dead DHCP server.
Besides a few articles in the press that have provided interesting public opinion, one enterprising person asked a few random non-attendees at the hotel what they thought of the event. The results are… enlightening.
How to communicate security risks to senior management
Despite the security industry getting ever more professional, with well trained teams, security incidents seem to be increasing. Just look at the news recently:
- Sony – 23 incidents so far?
- UK NHS Laptop – over 8 million patient records
- Citibank – 200,000 customer records lost
- WordPress platform vulnerabilities (see Steve Lord’s presentations on this)
- Stuxnet – targeted at a specific use
From the 2011 Verizon DBIR
- 761 breaches of which 87% were in Hospitality, Retail and Financial Services
- 436 of these were in companies with 11-100 employees – so this is not just a problem for the big targets any more
- 92% of attacks (leading to 99% of records compromised) were external
Some new threat groups:
Anonymous and LulzSec – often punitive, sometimes for the Lulz
- HBGary
- ACS Law
- Spanish Police
- FBI, CIA
- Porn sites
- Took requests
So what do the security professionals do?
- After an audit fix vulnerabilities
- After an attack, fix the issues
- Use encryption and strong authentication
- Patch regularly
- Validate input, encode output
- Assess your 3rd parties
- Use a Secure Development Lifecycle
- Build security into everything you do
No problem, right? If only it were that easy…
Your CEO wants the business to make money, so wants to minimise bottom line spend but will spend appropriately on risks to the business.
So why doesn’t the CEO see these security issues as business risks?
- Maybe they aren’t significant when compared to other business risks
- Or perhaps the CEO just doesn’t understand the latest security threat
Both of these are your problems. The security community is often called the ‘echo chamber’ for a good reason – we say good things and have good ideas about how to fix security issues, but we pretty much only communicate with other enlightened security professionals. We need to tell others in a way they can understand – but in general we talk technical 1337 speak full of jargon and no one can make head or tail of it.
It is up to you, the security professional to learn how to talk the language of business risk
There are materials out there that will help you:
- IIA GAIT – Guide to the Assessment of IT Risk
- FAIR – Factor Analysis of Information Risk
- ISACA CobIT – Control Objectives in IT
- ISACA – CRISC and CGEIT certifications
- IISP – approved Information Risk Management courses
Begin to understand what is important to a business executive and how they talk about it, and you are already well on the way to being able to articulate security in the same way. If you are a manager of security professionals, make it easy for them to gain exposure to heads of business, C-suite, executive, directors etc. and it is likely to benefit you in the long run.
These are good questions to prepare you for conversations you may have along the way
- What metrics should a CIO rely on to gauge risk
- How would you work with the security paranoiac on your team
- Can you provide loss values on security breaches
- How do you compare risks from website, physical perimeter, staff, etc.
- What are good threats to kick off conversations with others about what worries them